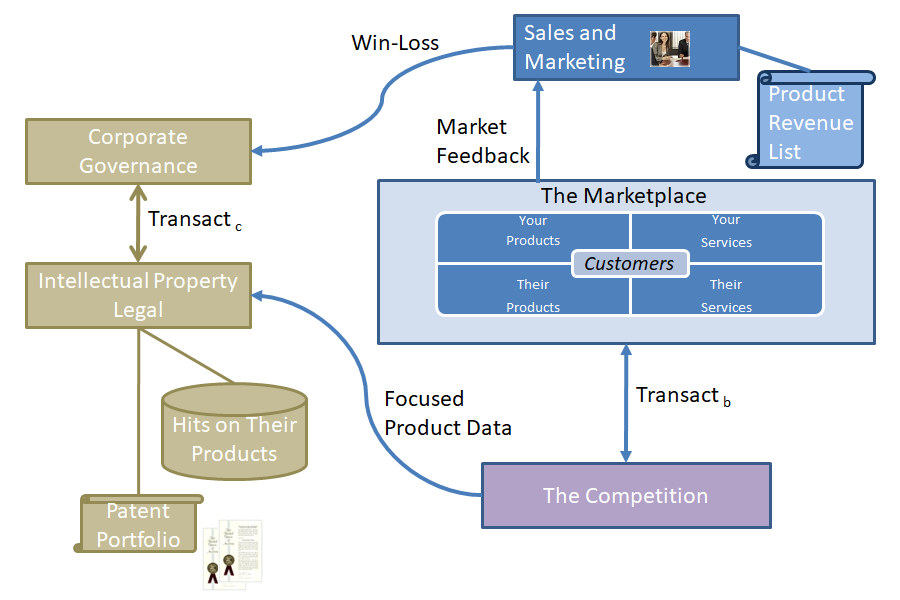
EXECUTING AN IP PROGRAM
Adopting and executing an IP protection program requires a combination of resource allocations and ongoing programs to keep cheaters in check. Applying a program that executes this, even at a basic level, is “a given” for most enterprises, especially those who market products with some degree of technical content.
Below are the basics of how this process works in a typical IP program:
Assertions
When asserting an IP infringement claim, the first order of business is for the IP owner to put the infringing party on notice. This must show the “areas of infringement” to the infringing party. It is the first step in an IP case and puts the infringing party on notice; the repartee begins.
This notice points out the exact parts of a product or service offering that infringes. The company then reviews the infringing party’s response (if there is one initially) to support the best action that is necessary to recover damages.
Defenses
Please note that this can work the other way too. In this case, a company receives notice from someone concerning an infringement on another party’s IP. It is not wise to ignore these claims and a prompt response is the first order of business. As with assertions, this is when the repartee begins.
There are a variety of possible responses to these claims. It is up to the company to decide the best course of action then to execute it. As with many legal matters, the path forward does not always continue predictably.
However, this paper is about assertions, not defenses. Using an IP Group to develop and execute defense strategies is a separate topic.